Proposed Title :
FPGA Implementation of wallet transform and bit plane slicing based Image Watermarking algorithm
Improvement of this Project:
Image Watermarking Algorithm procedure consists of four stages: structuring watermark, watermark embedding, processing watermarked image, extracting watermark.
Software implementation:
- Modelsim
- Xilinx 14.2
Proposed System:
Watermarking procedure consists of four stages: structuring watermark, watermark embedding, processing watermarked image, extracting watermark.
The DWT and IDWT approach followed is based on Haar wavelet transform which uses the following equations:
The equations used for determining the approximation (high) and detailed (low) component during forward transform and even and odd components (pixels) of the image during the inverse transform are:
The paper implements the algorithm in three stages:
Stage 1: This watermark embedding stage consists of generating watermarked image from the host image and watermark image with the help of Haar based DWT and BPS
Stage 2: The processing watermarked image stage where the watermarked image is attacked to check for its robustness under different extreme conditions prevailing over transmission media.
Stage 3: The watermark extraction stage consists of extracting watermark image from watermarked image without the usage of original image.
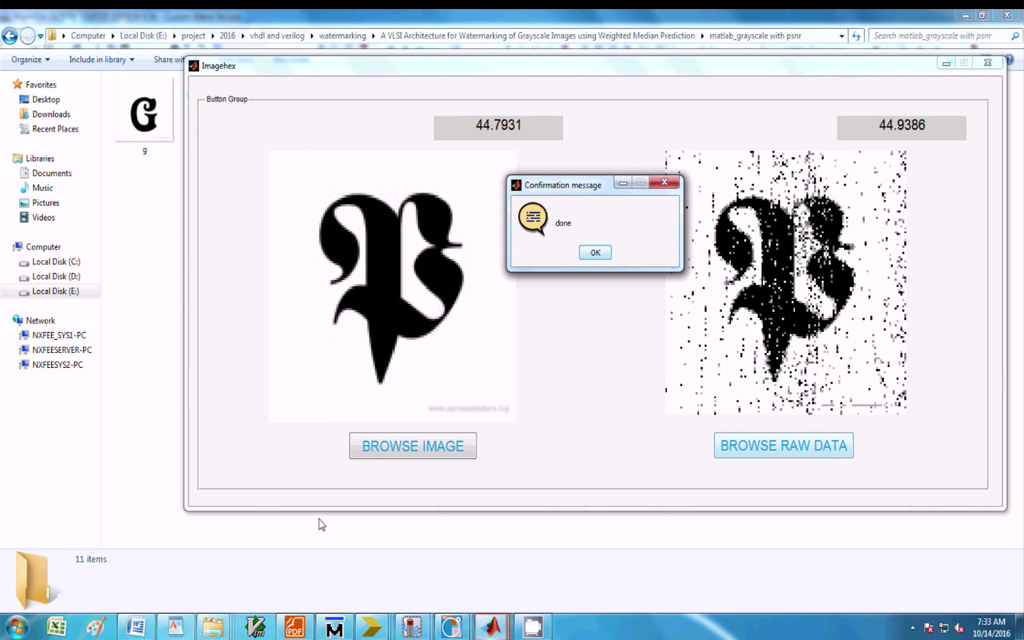
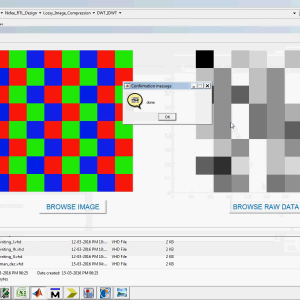
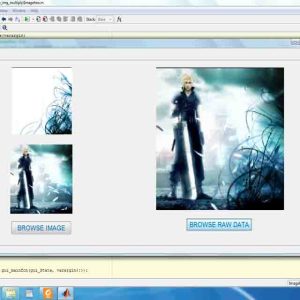
The flowchart depicting the procedure for embedding watermark in host image during image watermarking process using HL coefficients is shown in Fig 4 and same is followed for LH embedding. In this process the original gray scale image is transformed using frequency domain DWT to obtain HH, HL, LL, LH coefficients and then watermark is inserted in the suitable coefficients of transformed host image using spatial domain bit plane slicing. Then it is again back transformed or inversely transformed to generate watermarked image.
The HH and LL quadrants are not used for embedding watermark as they do not provide a robust and reliable solution and also the extraction of watermark from watermarked image is not possible under various circumstances. This paper draws a comparative analysis based on image quality measures for watermark embedded in HL and LH quadrants.
In extraction process the watermarked image is taken and transformed using DWT Haar equations mentioned previously and the coefficients for HH, HL, LH and LL are obtained. Using the pixel values of quadrant LH, the lower 4 bits of each pixel is extracted and used as higher 4 bits of pixel values of watermark image for the formation of extracted watermark image. The extraction process used in this technique is blind, that is during extraction the original image is not used to obtain the watermark from the watermarked image.
” Thanks for Visit this project Pages – Buy It Soon “
VLSI Implementation of Efficient Image Watermarking Algorithm
“Buy VLSI Projects On On-Line”
Terms & Conditions:
- Customer are advice to watch the project video file output, before the payment to test the requirement, correction will be applicable.
- After payment, if any correction in the Project is accepted, but requirement changes is applicable with updated charges based upon the requirement.
- After payment the student having doubts, correction, software error, hardware errors, coding doubts are accepted.
- Online support will not be given more than 3 times.
- On first time explanations we can provide completely with video file support, other 2 we can provide doubt clarifications only.
- If any Issue on Software license / System Error we can support and rectify that within end of the day.
- Extra Charges For duplicate bill copy. Bill must be paid in full, No part payment will be accepted.
- After payment, to must send the payment receipt to our email id.
- Powered by NXFEE INNOVATION, Pondicherry.
Payment Method :
- Pay Add to Cart Method on this Page
- Deposit Cash/Cheque on our a/c.
- Pay Google Pay/Phone Pay : +91 9789443203
- Send Cheque through courier
- Visit our office directly
- Pay using Paypal : Click here to get NXFEE-PayPal link

Reviews
There are no reviews yet.