Proposed Title :
FPGA Implementation of Obfuscating DSP Circuits based approach on Reconfigurable Folded Third order IIR Filter
Proposed System:
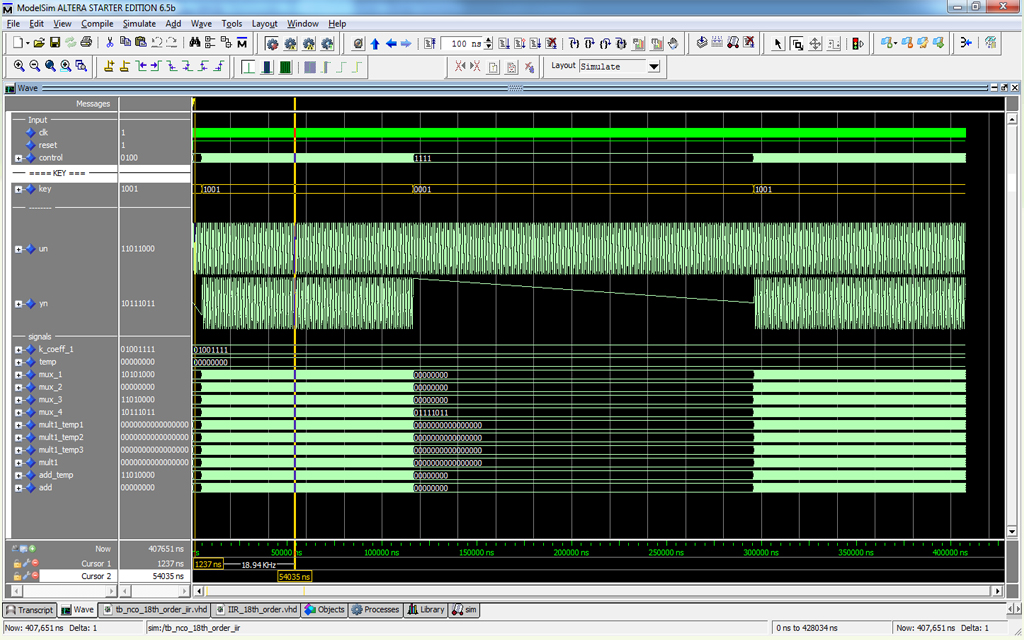
- Increase the sampling frequency, and tested cut-off frequency, with low pass, high pass, etc,.
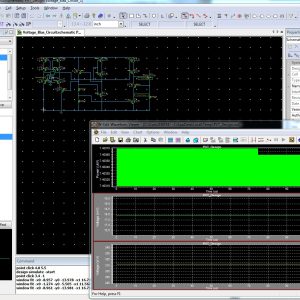
- Added digital control oscillator, and tested the power level with signal based.
Advantages:
- Reduce the power level
- Reduced the area size
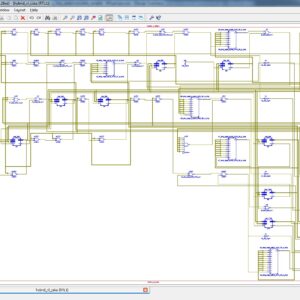
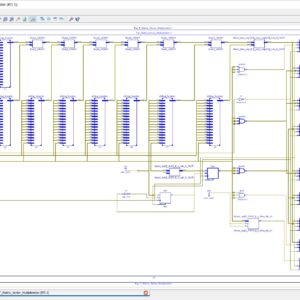
Software implementation:
- Modelsim
- Xilinx

Reviews
There are no reviews yet.